First Class Info About How To Detect Buffer Overflows
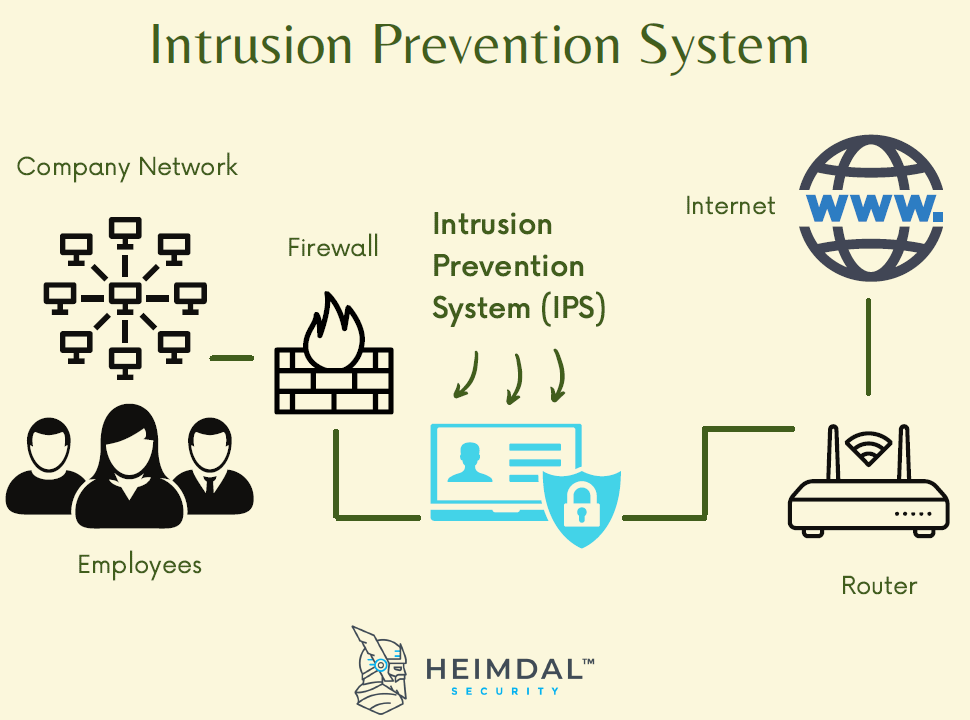
Thankfully buffer overflows can be prevented using a number of methods including:
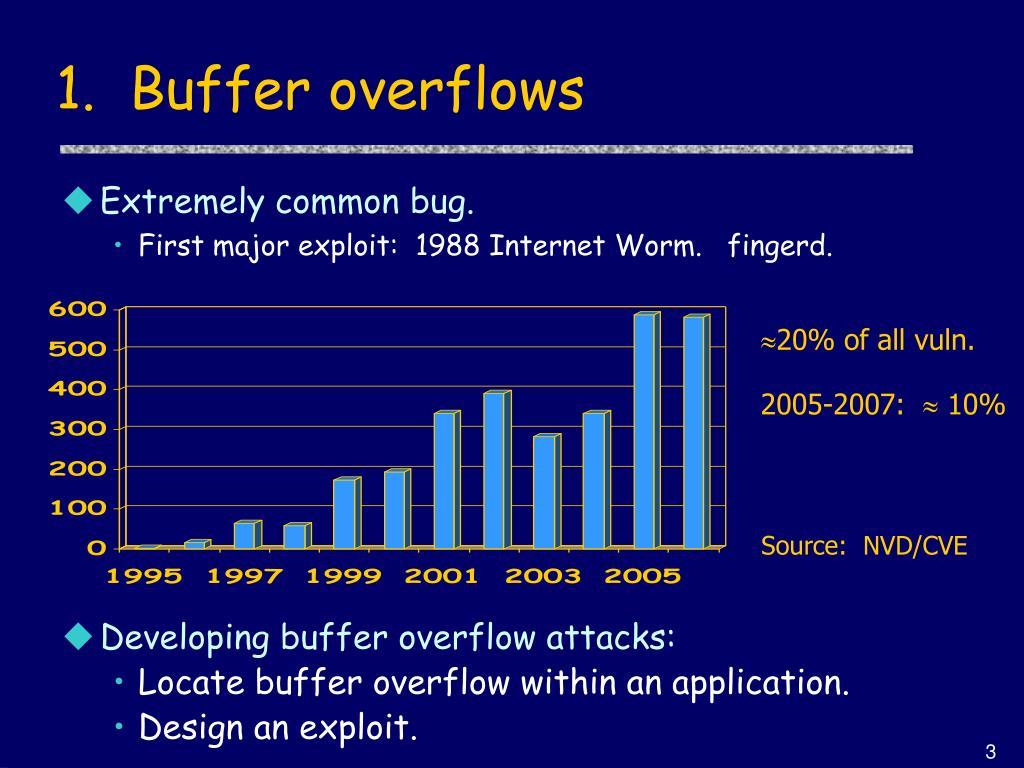
How to detect buffer overflows. Compiling with tools such as. Technical description a buffer overflow occurs when data written to a buffer also corrupts data values in memory addresses adjacent to the destination buffer due to insufficient. Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate systems.
The extra data can overflow into adjacent memory locations,. A buffer overflow is a type of runtime error that allows a program to write past the end of a buffer or array — hence the name overflow— and corrupt adjacent memory. What is a buffer overflow attack?
We're here to help. Ask question asked 15 years ago modified 1 year, 1 month ago viewed 42k times 33 i have heard about a. Ransomware glossary thenet copy article link what is buffer overflow?
A buffer overflow (or buffer overrun) occurs when the volume of data exceeds the storage capacity of the memory buffer. The buffer overflow vulnerability occurs whenever data written to a buffer exceeds its size. Most software developers know what a buffer overflow vulnerability is, but.
What c/c++ tools can check for buffer overflows? As a result, the program attempting. Buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s.
What is a buffer overflow and how do i cause one? Description buffer overflow is probably the best known form of software security vulnerability. Gcc how to detect stack buffer overflow ask question asked 10 years, 4 months ago modified 2 years, 6 months ago viewed 18k times 10 since there is an.
Read on to learn how they work and then identify best practices during. [closed] asked 15 years, 4 months ago. To successfully mitigate buffer overflow attacks, it is important to understand how they unfold.
Read on to see what a buffer overflow attack is, and what your organization can do to stop these threats. Nevertheless, aggressors have figured out.
![[VT detect] StackBased Buffer Overflows on Windows x86 Assessment](https://europe1.discourse-cdn.com/hackthebox/original/3X/f/2/f28b1e7635d4ecd8fea0ebbc0b6d0edcf1c05244.png)