Looking Good Info About How To Prevent Arp Spoofing

Click security > arp attack protection.
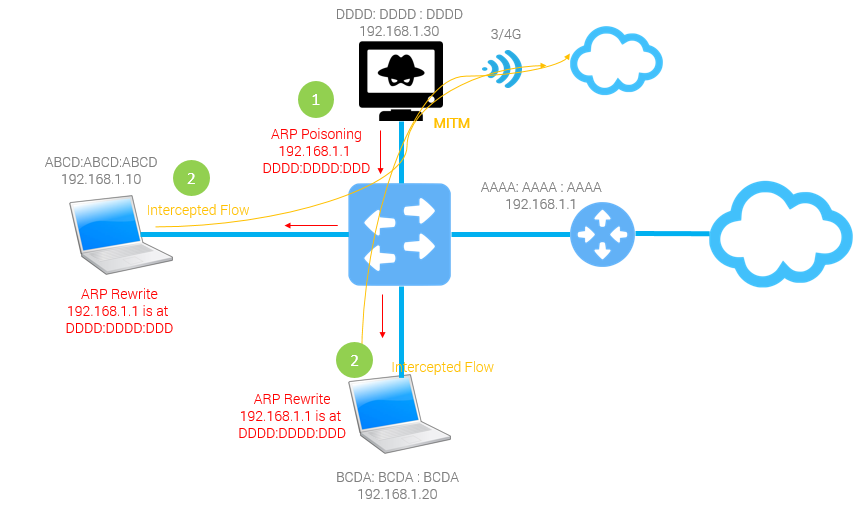
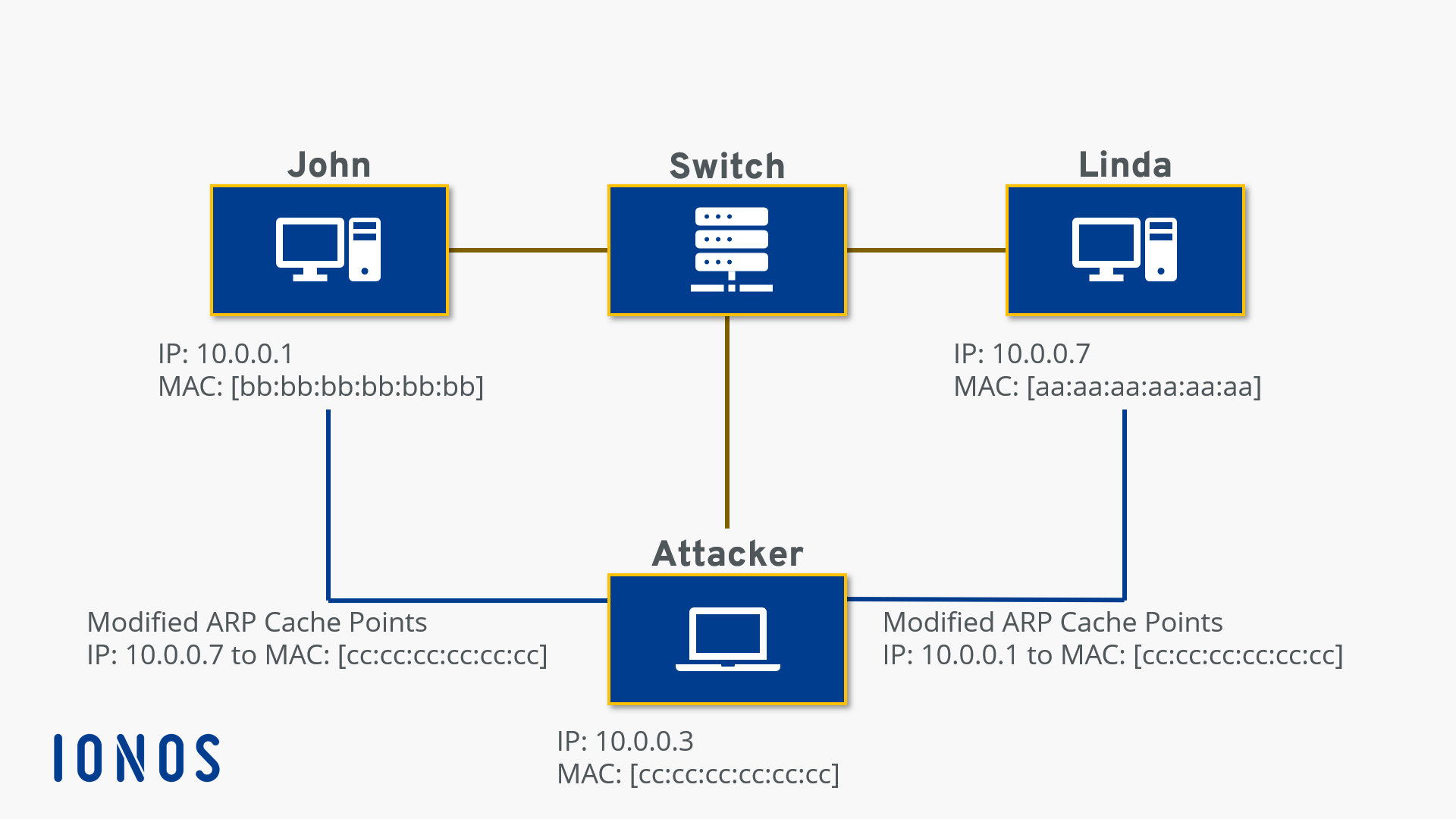
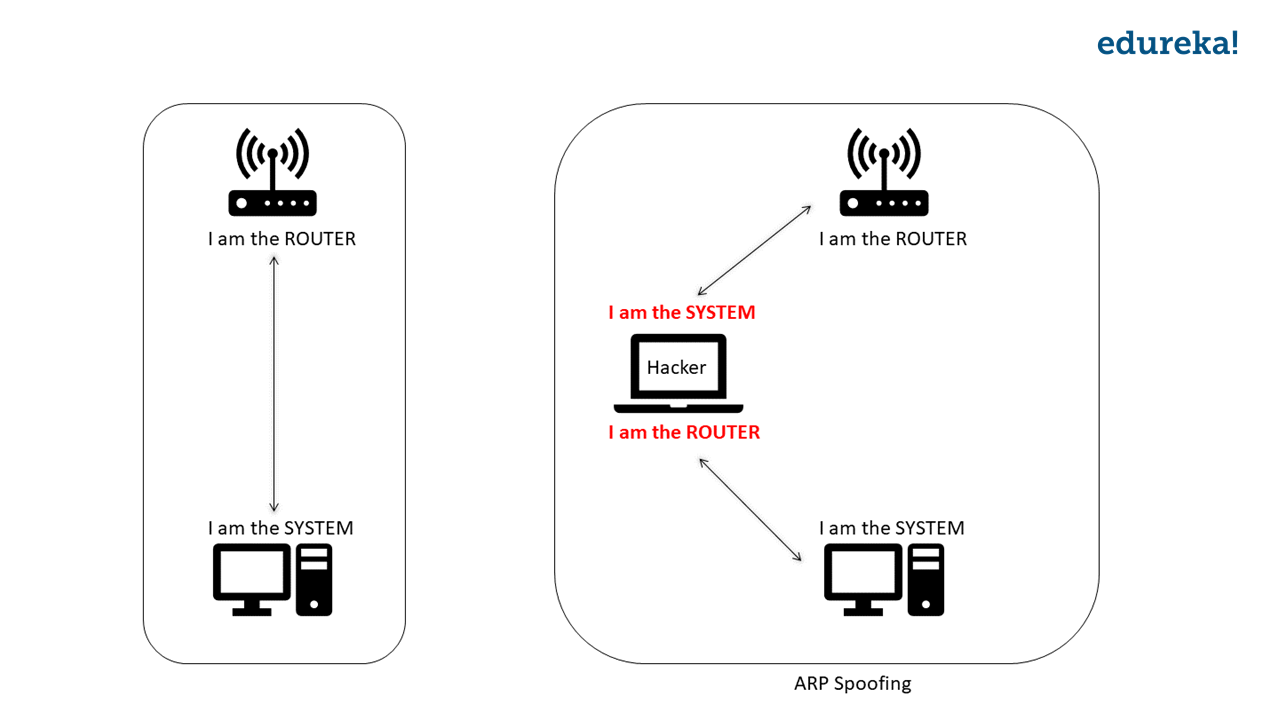
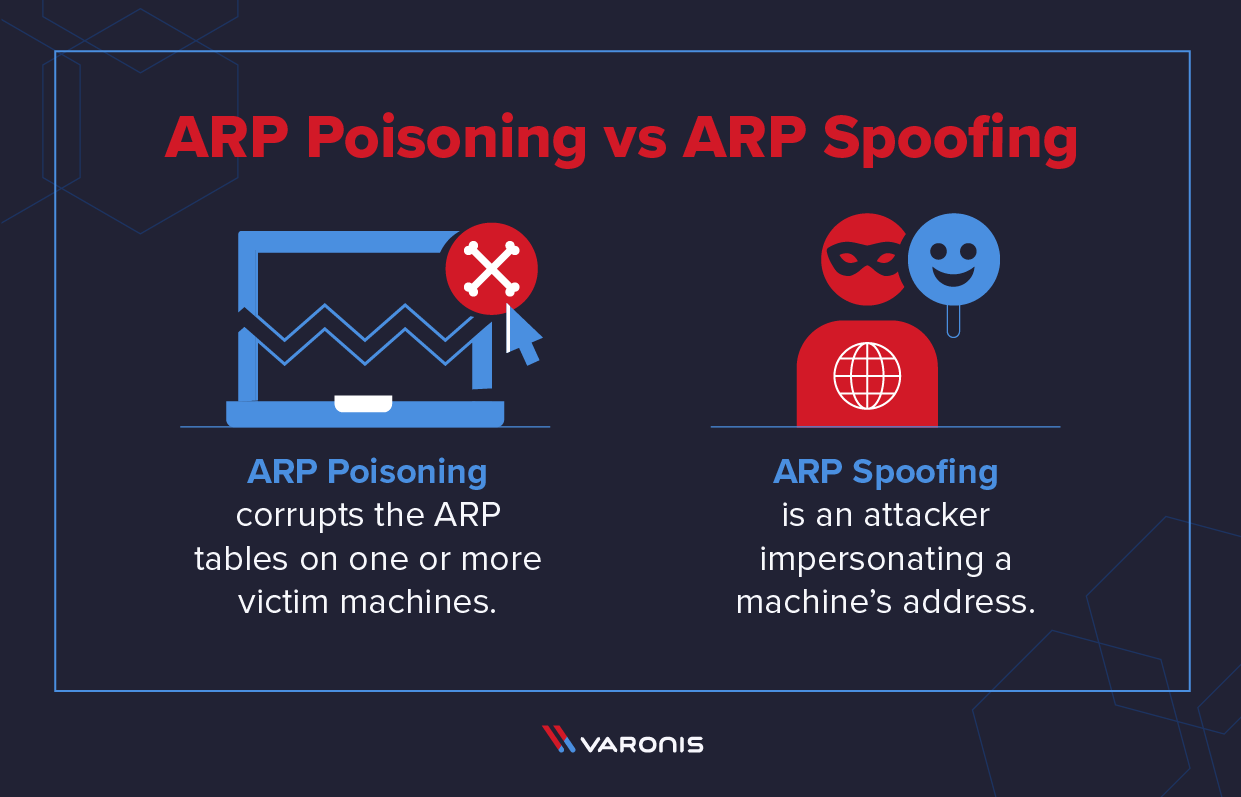
How to prevent arp spoofing. Technically, spoofing refers to an. It is used to convert ip address to physical addresses [mac. Arp spoofing vs arp poisoning.
To fully understand what arp spoofing is and how it works, we first need to know. The terms arp spoofing and arp poisoning are generally used interchangeably. It is important to remember that in order to initiate arp spoofing or arp poisoning attacks, a hacker can either wait to receive arp requests and provide a.
Detection and prevention software. How to protect your systems from arp spoofing. Way to prevent arp spoofing is to create a static arp table on a device, which will be loaded into ram everytime the operating system is.
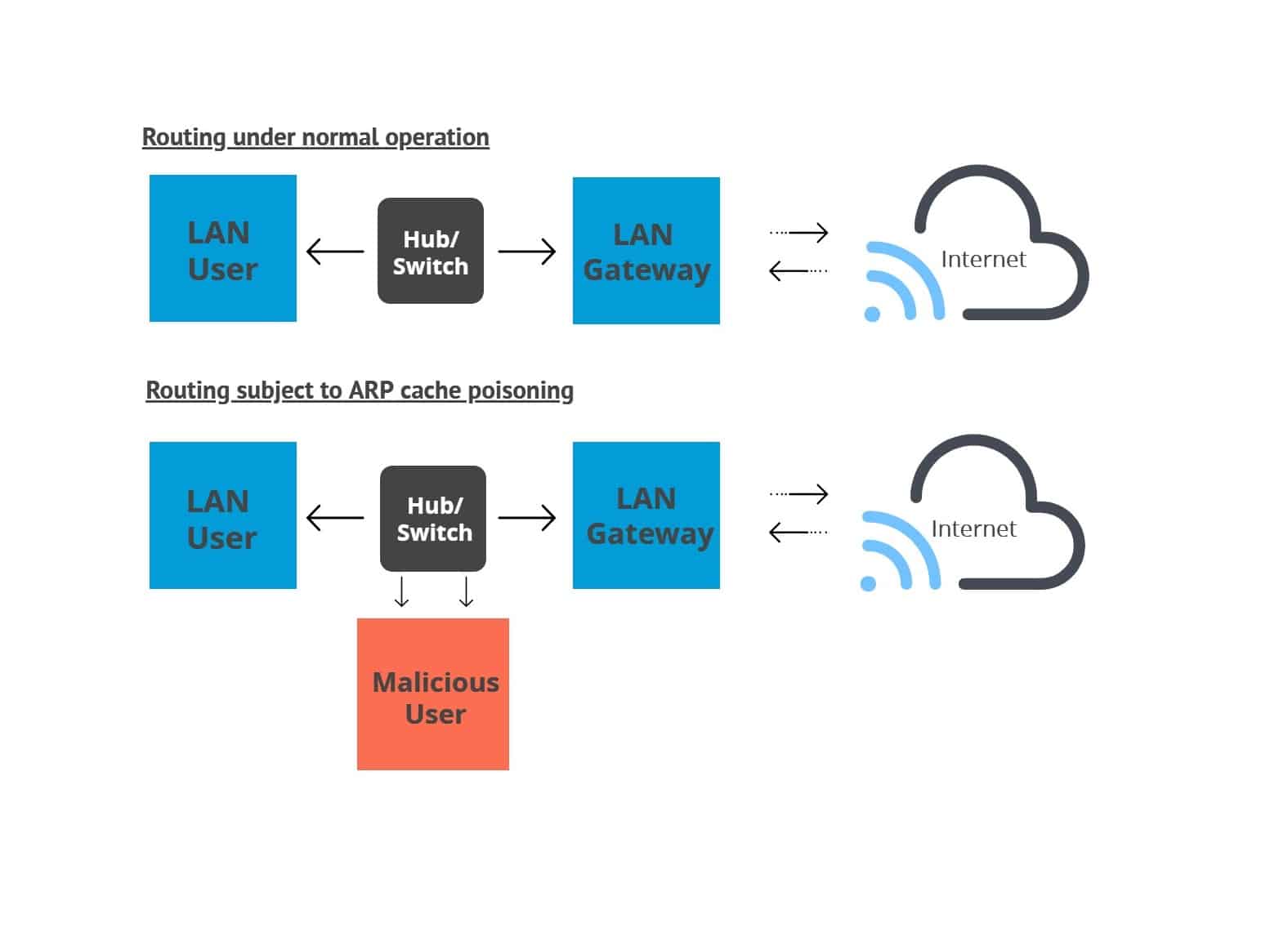
Arp information is never routed beyond the local subnet, so there is no possibility of an arp spoofing attack coming from outside the current network. And most importantly, how can you prevent it? / arp spoofing or arp poisoning.
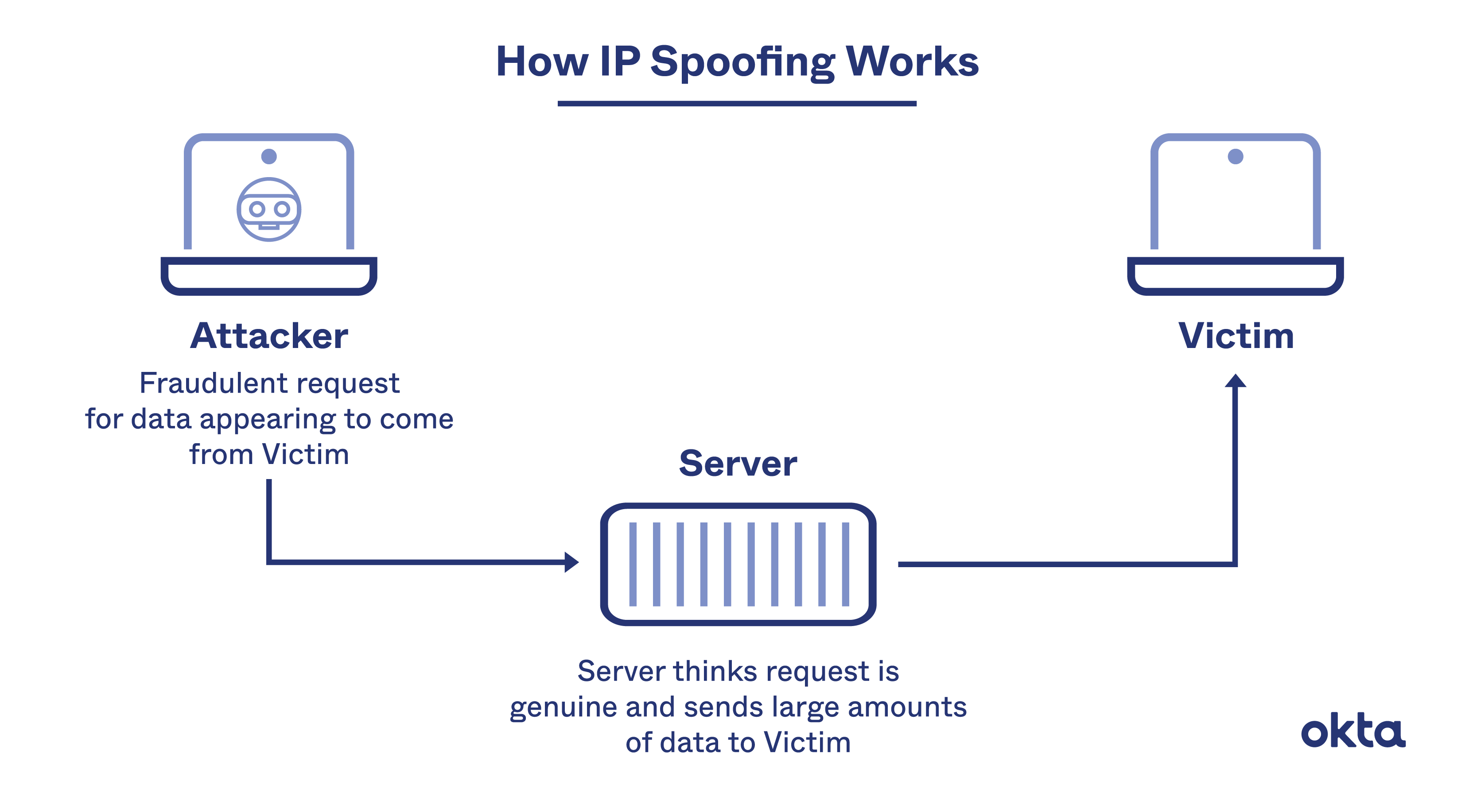
With thousands of spoofing attacks occurring every day, it’s become crucial to understand spoofing its types, and, of course, the ways to detect. When you connect to the internet, you typically first. One way to prevent arp spoofing from happening in the first place is to rely on virtual private networks (vpns).
By easydmarc on april 11, 2022. What is arp poisoning (arp spoofing) arp is the acronym for address resolution protocol. Continue reading to learn more about spoofing attacks, the seven common types of spoofing attacks and how to stay protected from them.
Address resolution protocol (arp) spoofing, also referred to as arp cache poisoning or arp poison routing, refers to an invasive attack. The arp attack protection page opens. Address resolution protocol (arp) poisoning is a seizure.
The arp spoofing attack, also known as arp poisoning, is a technique used to attack local networks. How to detect and prevent arp spoofing? Attackers can modify or inject malicious data into network traffic, potentially leading to unauthorized access or system compromise.
To prevent arp attacks and configure the ip&mac binding settings: